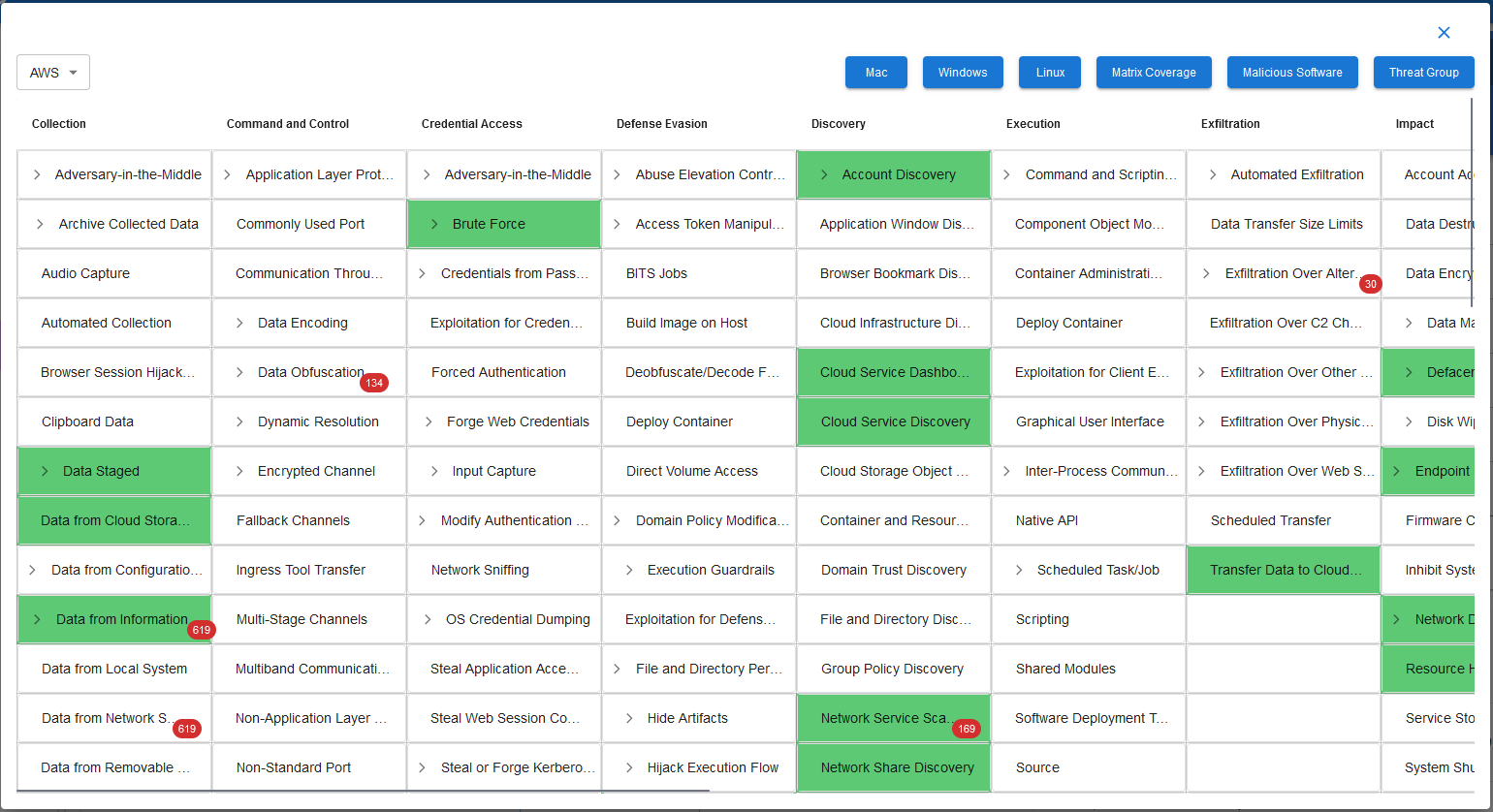
CyberMon integrates with the MITRE ATT&CK
framework to enhance its threat detection, analysis,
and response capabilities. MITRE ATT&CK is a knowledge base of adversary tactics, techniques, and
procedures (TTPs) based on real-world observations. By incorporating MITRE ATT&CK, CyberMon
leverages a structured and comprehensive resource to improve threat identification, incident
response, and security posture.
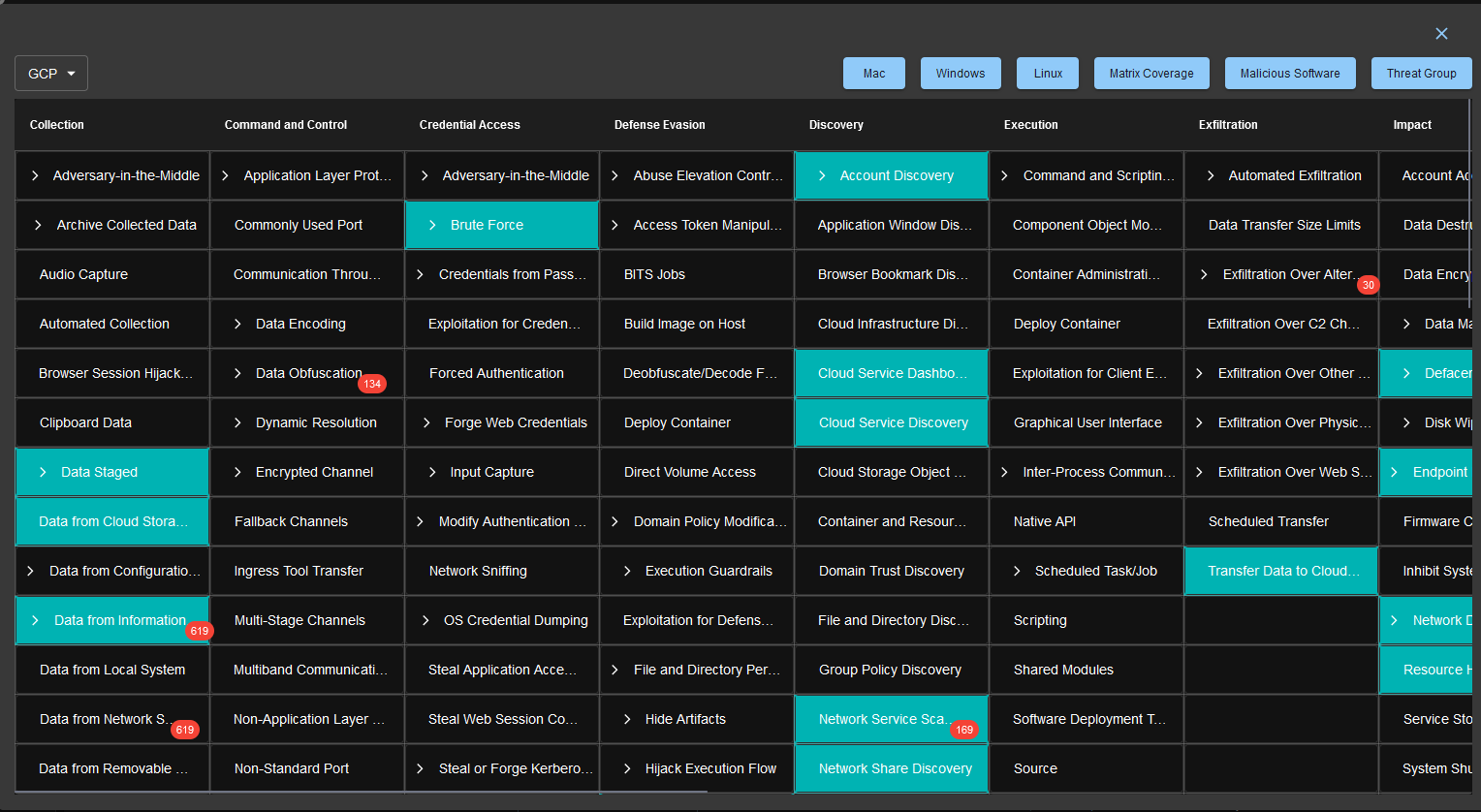
Threat Intelligence Mapping
CyberMon integrates the MITRE ATT&CK framework to map observed security events and activities to known adversary tactics and techniques. This helps in contextualizing alerts and incidents by aligning them with specific TTPs documented in the MITRE ATT&CK matrix.
Enhanced Threat Detection
By referencing MITRE ATT&CK, CyberMon enhances its threat detection capabilities. It uses the
framework to identify and classify suspicious activities based on known attack patterns, improving
the accuracy and relevance of alerts.
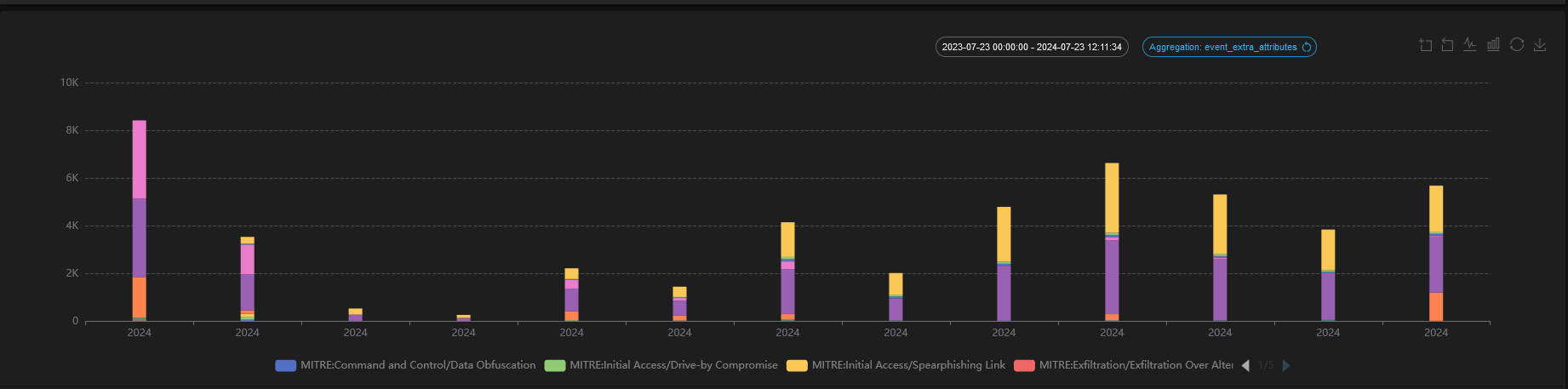
Incident Analysis and Investigation
The integration allows CyberMon to utilize MITRE ATT&CK techniques to analyze and investigate security incidents. It provides a structured approach to understanding how an attack might have unfolded, what tactics and techniques were used, and what indicators of compromise (IoCs) to look for.
Tactical and Strategic Reporting
CyberMon leverages the MITRE ATT&CK framework to generate detailed reports on security incidents, including the tactics and techniques used by adversaries. These reports provide actionable insights for improving defenses and understanding the threat landscape.
Security Control
CyberMon uses MITRE ATT&CK to assess the effectiveness of existing security controls and measures. By mapping the framework’s techniques to the organization’s controls, CyberMon can identify areas where additional defenses may be needed.
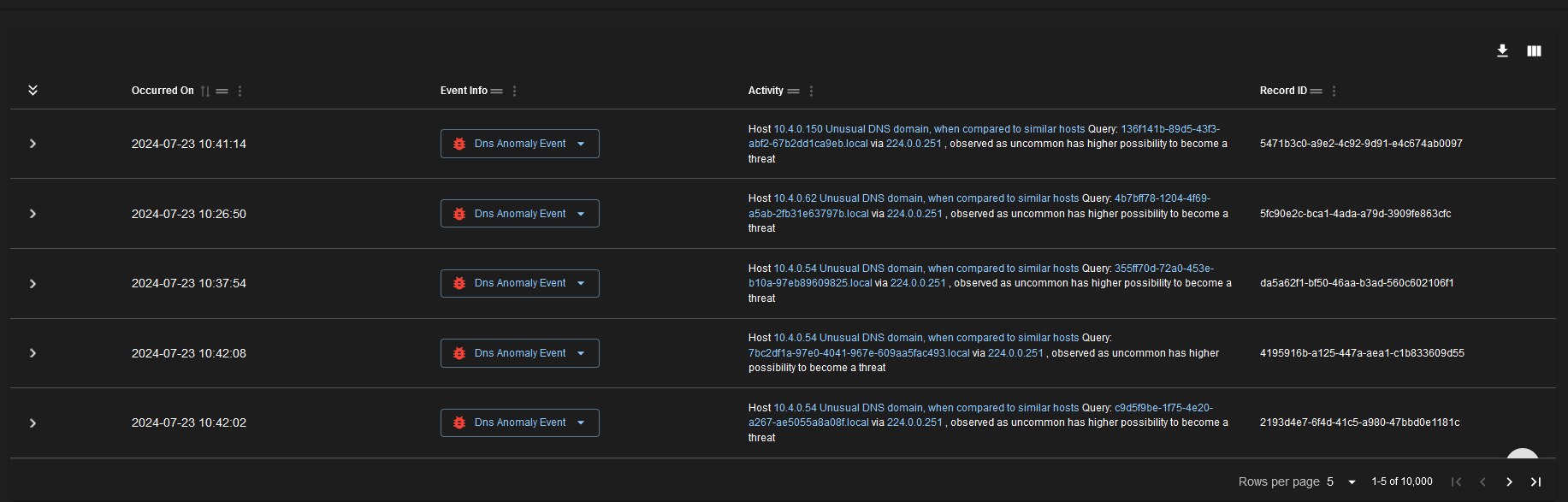
Continuous Improvement
MITRE ATT&CK provides a dynamic and evolving knowledge base of adversary tactics and techniques. CyberMon uses this up-to-date information to continuously refine and improve its threat detection and incident response processes.