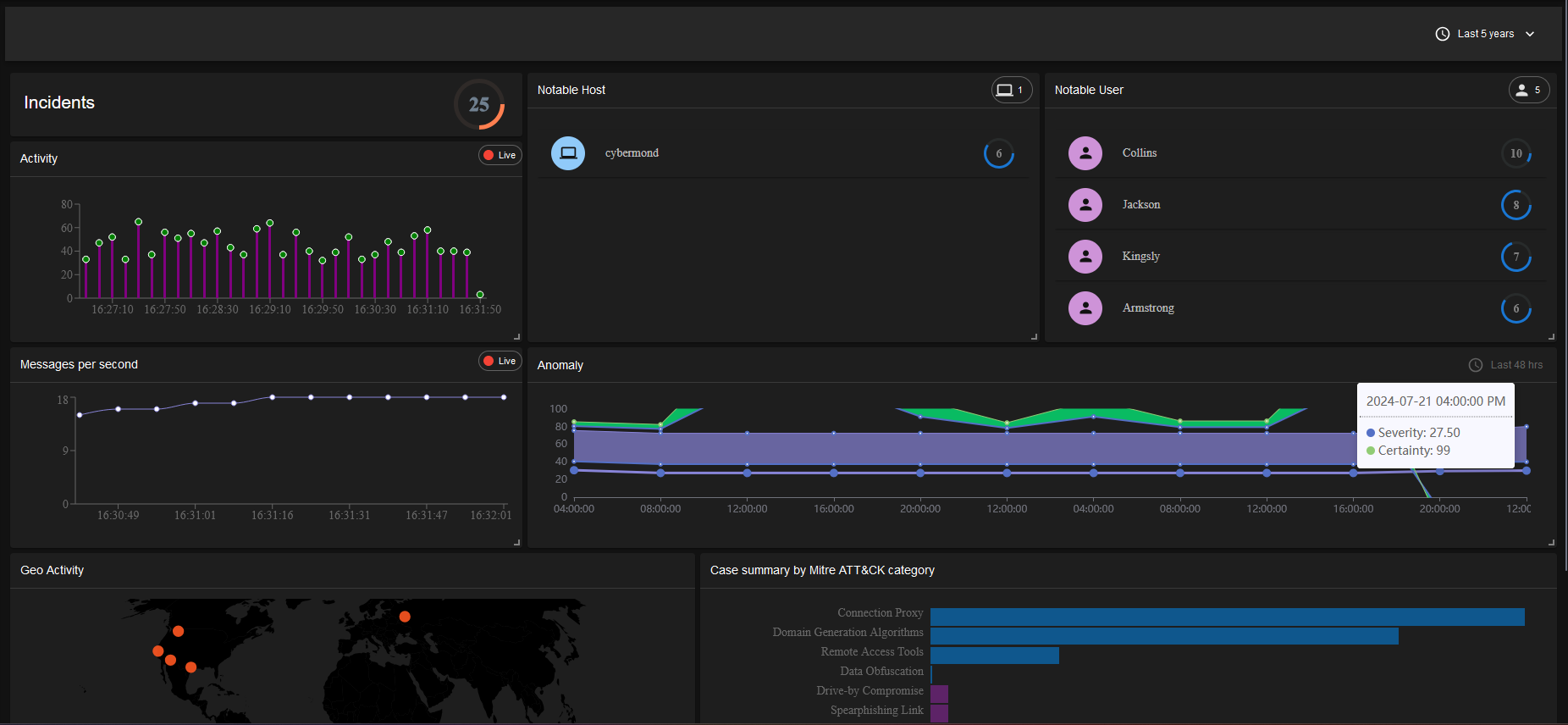
The CyberMon dashboard provides a comprehensive view of cybersecurity metrics, including incident
count, activity, notable hosts and users, messages per second, anomaly geo-activity, and case
summaries categorized by MITRE ATT&CK.
Incident Count
- Tracks the total number of security incidents detected over a specified period, giving an overview of the threat landscape and allowing for trend analysis.
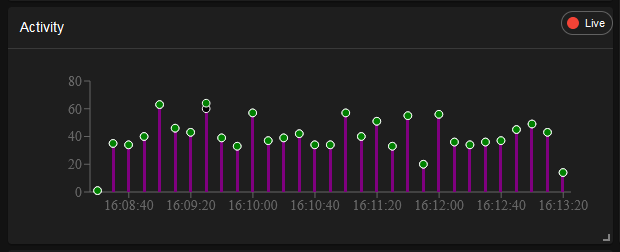
Activity
Displays the volume and type of network and system activities, helping to identify normal versus suspicious behavior.
Notable Hosts
Highlights specific hosts that have exhibited significant or unusual activity, indicating potential security concerns or targets for further investigation.
Notable Users
Highlights specific users that have exhibited significant or unusual activity, indicating potential security concerns or targets for further investigation.
Messages per Second
Measures the rate at which messages are being processed by the system, providing insights into network load and performance.
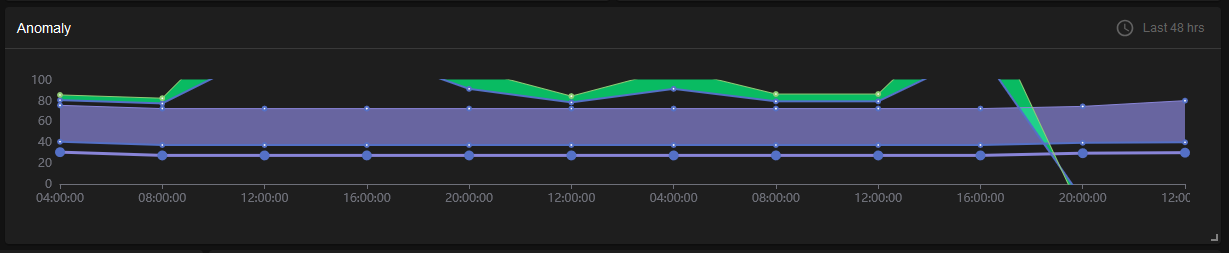
Anomaly
Detects and reports on unusual patterns or deviations from normal behavior, indicating potential security threats or breaches.
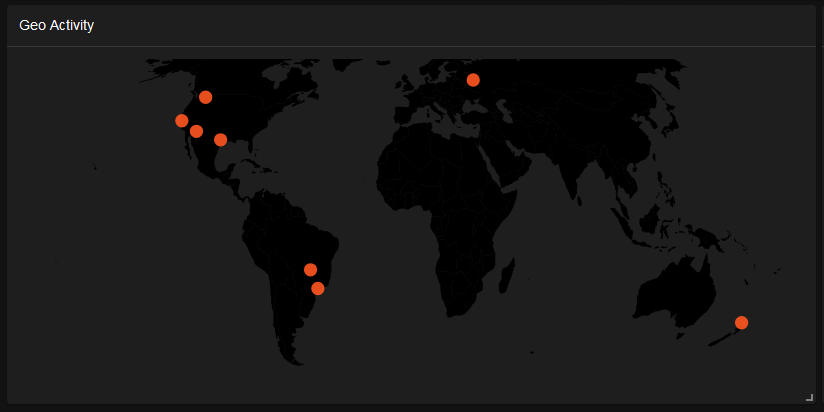
Geo-Activity
Maps the geographical locations of network activities, allowing for the visualization of potential threat sources and patterns based on geographic data.
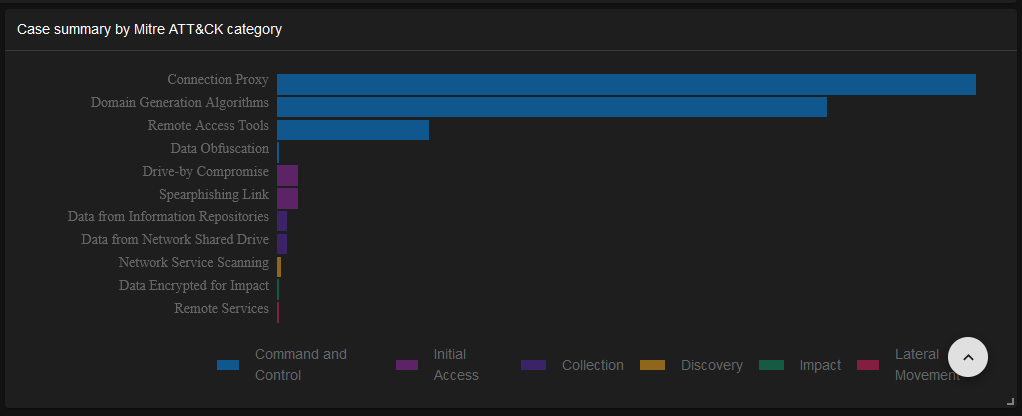
Case Summary by MITRE ATT&CK Category
Summarizes cases according to the MITRE ATT&CK framework, categorizing incidents based on known attack techniques and tactics, aiding in understanding and mitigating specific threat vectors.